My company Foundeo Inc. released a new free web service today called HackMyCF that allows you to scan your ColdFusion server to detect the absence of recent ColdFusion security hotfixes as well as other security problems.
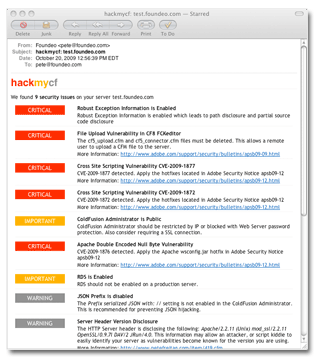
The site generates an email report detailing what security issues were found, here's an example:
I would love to hear your feedback!
BTW, we now have a CFML Code Security Scanner called Fixinator!
Comments
I have yet to try this out, but I think this is an amazing idea! Thanks for putting in the time and effort to make it publicly available.
Concerning the "Server Software Disclosure" warning, here's an article that describes how to change the server header in IIS7. http://blogs.technet.com/stefan_gossner/archive/2008/03/12/iis-7-how-to-send-a-custom-server-http-header.aspx The comments also contain an interesting discussion of whether this is really necessary from a security standpoint, and some insinuations about why Microsoft didn't make this a simple change.
Darn it, I meant to say concerning the "Server Header Version Disclosure" warning. The "Server Software Disclosure" is a simple change in IIS.
@Gary - The FCKeditor vulnerability is an important one, it is installed as part of ColdFusion 8, and is located under /CFIDE/ See http://www.petefreitag.com/item/704.cfm for more info.
@Mark thanks! @steveeray would you mind emailing me your server domain so I can look into it. Is it possible that some files still existed in your CFIDE after the update. @David great link, thanks!
@David, it looks like that latest version of Microsoft URLScan supports IIS 7 / Windows 2008: http://www.iis.net/extensions/UrlScan
I love this. Great idea! I never knew I needed to apply an Apache patch. Unfortunately I have some other servers I would like to check but I do not have an E-mail address at those domains since our work E-mails are all on a secondary domain that the site doesn't operate on. Is there a way I can check those?
@Brad, yes I added a feature that allows you to use any email address provided that you can create a temporary file in the web root using a certain file name. Just enter the domain and email and it will tell you how to do it.
Hi Pete- I ran HackMyCf before I applied any security patches on my 8.01 server yet it found nothing. Could it be because I have CFAdmin behind a firewall or an alternate port.
Doug - yes if it can't find /CFIDE then it really limits what it can find. But that is a good thing!
Does that mean I do not need to apply these patches since I have secured CFIDE. We have always moved them to an alternate port and left that without public access. Only someone on our VPN can see it which is extremely limited. I have a second question as well. In our PCI Compliance we found we were open to XSS attacks on our forms. One of the developers wrote something that escapes <>" and "" and the example code the compliance company sent no longer works. I know this is a stretch to answer but if we prevent those characters could that be the end of the PCI Compliance certification issue. IT seems too easy.
@Doug: No need to write you own functions. Use the HTMLEditFormat() function to make a string safe to include in HTML, and use the jsStringFormat() function to make a string safe for JavaScript. Properly escaping ALL user-controlled strings on your site is neccessary to prevent XSS.
@Doug - I would still recommend applying the patches even if our remote tool can't find them it doesn't mean a hacker can't. As for the XSS, you really need to remove more than just <>"' to be protected in all cases and HTMLEditFormat doesn't totally do the trick, for example HTMLEditFormat doesn't escape single quotes. To be free of XSS concerns you need to strip out <>'"();#