Web Application Firewall for ColdFusion Launched
By Pete Freitag
I'm excited to announce today the launch of Foundeo's latest product: the Foundeo Web Application Firewall for ColdFusion. The product can block or log malicious requests to your ColdFusion applications. Including things like:
- Cross Site Scripting / XSS
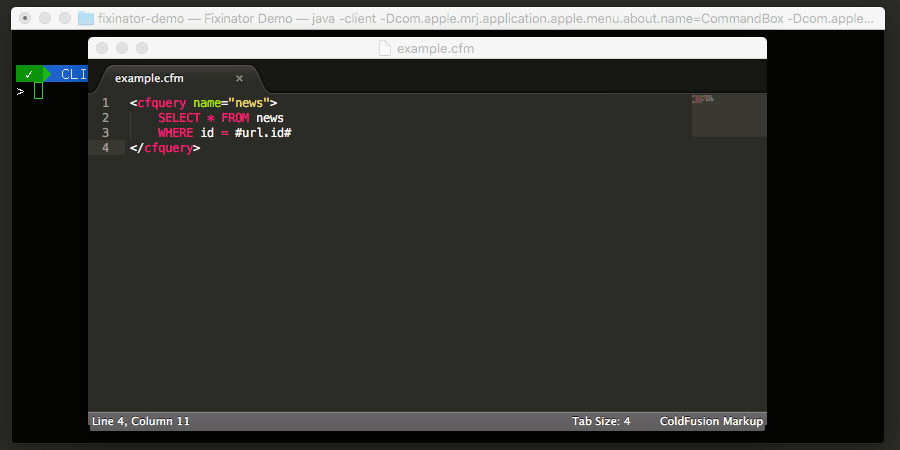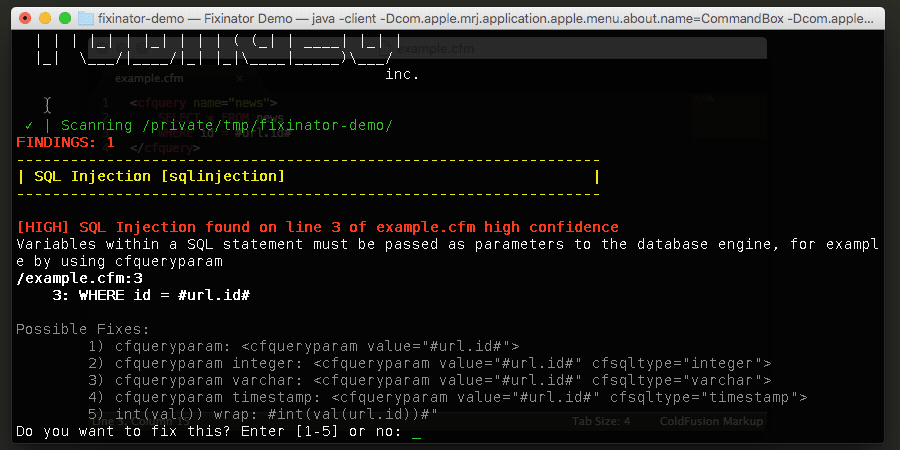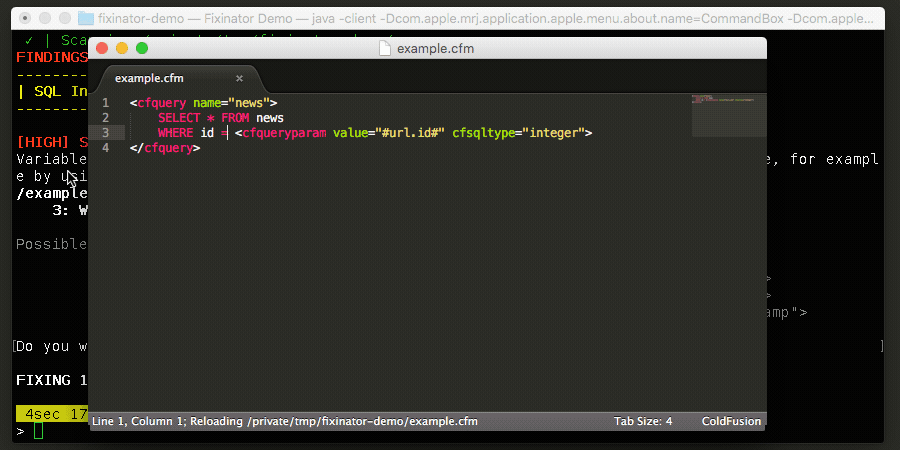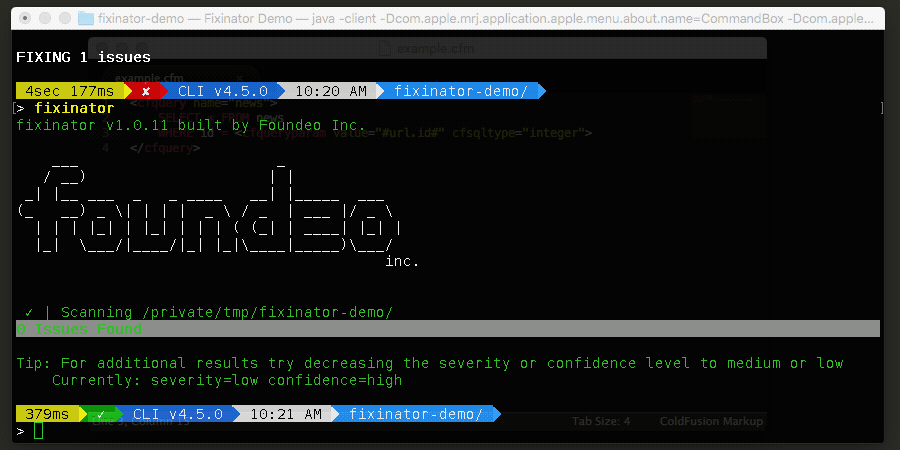
- SQL Injection
- Session Hijacking
- Cross Site Request Forgery
- CRLF Injection
- Path Traversal Attacks
- Password Dictionary Attacks
I think it is also important to address what this product is not. It is not a magic filter that can catch every possible hack attempt on your web applications. All you need is one security hole for a hacker to be successful. I want to make it very clear that this product should not be a substitute for secure coding practices. Infact we actually giving away a copy of our CFML Security Checklist with each copy the firewall we sell.
Because this product is written in CFML, there are some unique advantages, such as:
- You can use it on most Shared Hosting Accounts
- You can write your own custom Filters in CFML
- You can interact with the firewall directly from within your ColdFusion web applications.
- Configuration is done with CFML, no need to learn a new configuration language.
Twitter Contest - Win a Free Copy
We are also holding a twitter contest. Follow @foundeo on twitter by 4/1/09 for a chance to win. The winner will be picked randomly from all @foundeo followers on 4/1/09.
Web Application Firewall for ColdFusion Launched was first published on March 26, 2009.
If you like reading about security, firewall, waf, or foundeo then you might also like:
- Video: Installing FuseGuard
- Announcing FuseGuard Version 3
- FuseGuard 2.4 Released
- Adobe eSeminar on FuseGuard
The Fixinator Code Security Scanner for ColdFusion & CFML is an easy to use security tool that every CF developer can use. It can also easily integrate into CI for automatic scanning on every commit.
Try Fixinator
CFBreak
The weekly newsletter for the CFML Community
Comments
We don't have any It does not rewrite any cookies, it doesn't alter the request at all out of the box, but you could write filters that do that.
And the pricing on our enterprise version is actually much less than other WAF's, which can cost 10's of thousands of dollars. Also I don't think the Sonicwall appliance is a Web Application Firewall, but rather a more traditional network firewall.
Thank you for your interest.
(no cookie rewrite) Good. Portcullis destroyed all domain level cookies and I had to quit protecting cookies as a result.
(Pricing) I googled WAF and found "Woman Acceptance Factor" [grin]... but the first 2 results for "web application framework" were 2 open source solutions, OWASP and ModSecurity. I don't know too much about their offerings yet, but is there any additional information available concerning CWAF apart from the single page of information? I'd like to learn more, but don't want to have to think about which questions to ask or spend too much time contrasting and comparing it with other products.
Thanks.
I will admit the product page is still a bit sparse, but if you request an evaluation you can learn more about our product from the documentation. Also feel free to contact foundeo: http://foundeo.com/contact/ with any questions you might have.
One of the big differences is that our Firewall can be added and configured to the application by the developer. Setting up a proxy mod_security would have to be done by the systems and network administrator, who probably has much less knowledge of how the application actually works. In my opinion a WAF is best configured when it is done with a deep understanding of the web application it is protecting.
Also in many cases (most notably on shared hosts) you may not be able to external software or hardware. If you can run CFML you can use our firewall.
One final use case is blocking password dictionary attacks. Most WAF's can do this by seeing lots of password requests come in, but only the web application knows if it is an invalid username, or an invalid password. If someone is trying lots of invalid usernames you could provide a more aggressive blocking strategy. Sending this message from your CFML application to an external WAF can be difficult, sending a message to our WAF from your application is very easy.
All that being said this product is not a golden hammer, you need to pick the best tool for your needs.
 Pete Freitag
Pete Freitag