ColdFusion 8 Security Whitepaper
Published on July 31, 2007
By Pete Freitag
By Pete Freitag
Adobe has published a whitepaper called: ColdFusion 8 Product Security Briefing, which outlines the results of an independent security audit from Information Risk Management Plc.
The white paper is not very detailed, but here's a quick summary of their findings:
- New Authentication for CF Admin has raised the overall security of the product
- Server Monitoring Features - Exceeded industry standards
- Remote Debugging - Should be disabled on all internet facing servers
- AJAX Features - "AJAX introduces several potential security issues which can be attacked in new creative ways and also increases the likelihood of client side attacks in poor implementations. However, Adobe is aware of these attacks and has mitigated the risks associated with their exploitation."
- New Tags - Adheared to sandbox security model, tested with mailformed data.
- "In respect to code level security, the source code was well written and adhered to Sun Microsystems guidelines for writing secure code."
One line I did find to be curious was this one:
ColdFusion remote debugging relies on RDS (Remote Development Services) thereby leveraging security features provisioned by this tried and tested protocol.
ColdFusion 8 Security Whitepaper was first published on July 31, 2007.
If you like reading about coldfusion, security, coldfusion 8, or whitepaper then you might also like:
- Potential gotcha with searchImplicitScopes and cfparam
- Fixinator 6.1.0 - Detecting Undefined Remote Arguments
- The CWE 25 and ColdFusion - CFSummit East 2025 Slides
- ColdFusion Summit 2024 Slides: 20 ways to secure CF
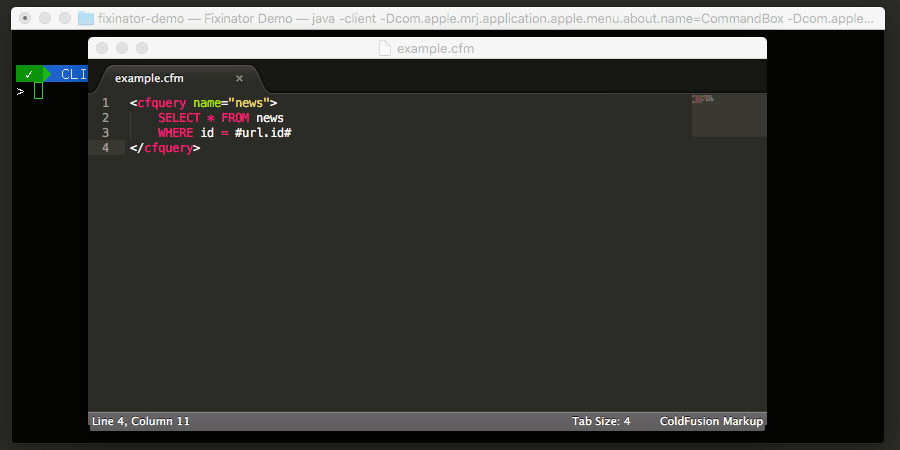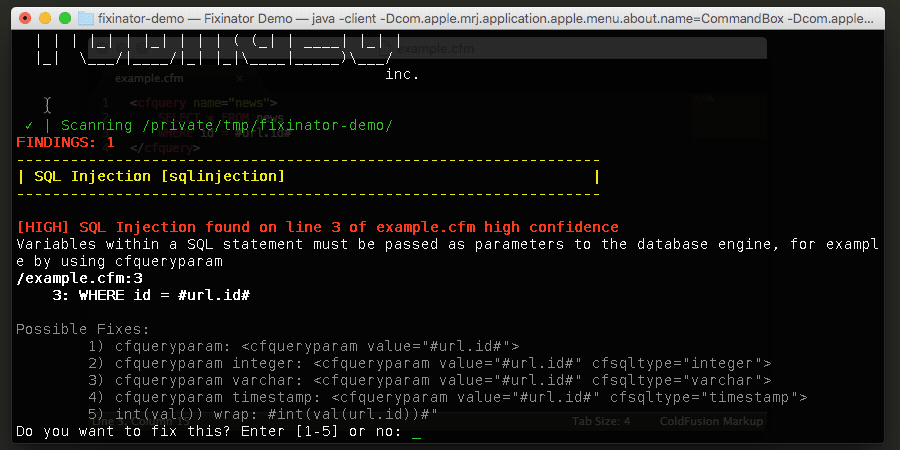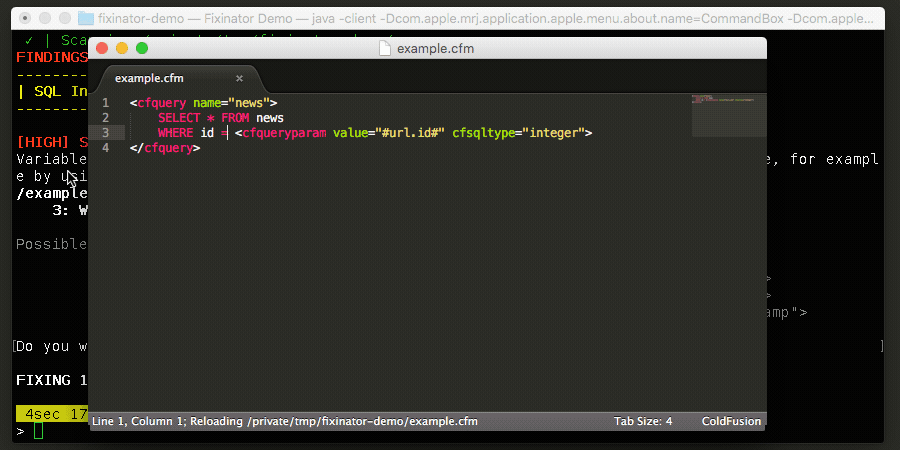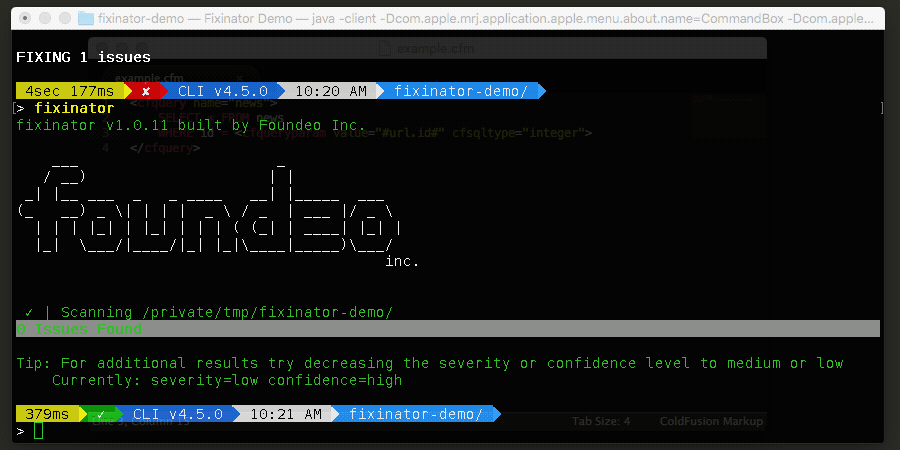
The Fixinator Code Security Scanner for ColdFusion & CFML is an easy to use security tool that every CF developer can use. It can also easily integrate into CI for automatic scanning on every commit.
Try Fixinator
CFBreak
The weekly newsletter for the CFML Community
Comments
Thanks for posting this. I'm doing a CF-Sec preso later today and this will come in handy. Some of the AJAX stuff they added (I mean security wise) is pretty cool. Have you looked into it yet? For example, there is now a secureJSOn attribute for cffunction, and a VerifyClient function. This isn't mentioned in the reference, just the dev guide. I'll be doing a blog entry on it later this week.
by Raymond Camden on 07/31/2007 at 1:03:15 PM UTC
Oops, it _is_ covered in the ref. I had a slight mix up with my various versions of the cf8 docs. ;) Either way though it was only added recently i believe.
by Raymond Camden on 07/31/2007 at 1:09:30 PM UTC
"One line I did find to be curious was this one"
Makes one wonder just how "independent" that security audit was, if they think RDS is a secure "tried and tested" protocol.
Makes one wonder just how "independent" that security audit was, if they think RDS is a secure "tried and tested" protocol.
by Jacob Munson on 07/31/2007 at 1:10:37 PM UTC
Ray, I haven't gotten into those features too much yet, but I will be taking a closer look now that you mention it.
by Pete Freitag on 07/31/2007 at 3:52:23 PM UTC
I'm not sure what to say other than their security findings are as independent as they come...
RDS is a highly secure protocol that has been around for a very very long time and has only been improved upon with each version. Don't dis the RDS! :)
The comment is related to the fact that spawning an open debugging port can cause security issues... with RDS, you can secure your server so that only the web server ports are open and still do your debugging. ;)
Jason
RDS is a highly secure protocol that has been around for a very very long time and has only been improved upon with each version. Don't dis the RDS! :)
The comment is related to the fact that spawning an open debugging port can cause security issues... with RDS, you can secure your server so that only the web server ports are open and still do your debugging. ;)
Jason
by Jason Delmore on 08/01/2007 at 6:45:19 PM UTC
@Jason, I read through most of the whitepaper, and parts of it sounded like ads right out of Adobe's press room.
Don't get me wrong, I love ColdFusion as much as the next guy. But I think "independent" is a little bit of a stretch in this case. It doesn't matter who's software we're talking about, this kind of thing happens all the time.
What happened here is that Adobe paid a security firm to audit ColdFusion. When that happens, the security firm wants to make Adobe happy. I mean, how are they going to keep getting hired by Adobe if they trash Adobe's software? I am not saying that CF has overlooked security problems, I'm just illustrating how these these things can stray from being independent. It doesn't always happen, but security firms are human too. :)
Don't get me wrong, I love ColdFusion as much as the next guy. But I think "independent" is a little bit of a stretch in this case. It doesn't matter who's software we're talking about, this kind of thing happens all the time.
What happened here is that Adobe paid a security firm to audit ColdFusion. When that happens, the security firm wants to make Adobe happy. I mean, how are they going to keep getting hired by Adobe if they trash Adobe's software? I am not saying that CF has overlooked security problems, I'm just illustrating how these these things can stray from being independent. It doesn't always happen, but security firms are human too. :)
by Jacob Munson on 08/01/2007 at 7:06:30 PM UTC
 Pete Freitag
Pete Freitag