10 Ideas to Improve Security in ColdFusion 10
Published on June 18, 2010
By Pete Freitag
By Pete Freitag
I do a lot of work related to security in ColdFusion and I've been keeping a list of ideas and features that could make a future version of ColdFusion more secure. Here's 10 ideas in no particular order:
- Add an
allowedextensionsattribute to cffile for action=upload and deprecate theacceptattribute - Theacceptattribute is useless as far as security goes since the mime types come from the client, you can easily spoof this (example). This new attribute would simply be a list of file extensions that you allow to be uploaded, eg "jpg,png,gif,jpeg". - Ask for a Windows Username to run ColdFusion services as during installation - The ColdFusion installer already does this on a unix install, but not windows. This should setup permissions on the ColdFusion installation directory.
- Update Documentation and verbage related to ScriptProtect so people don't think it completely protects you from XSS - It's a very weak protection, yet alot of people think it fully protects them. I think this is due to how it is worded in the CF Administrator and documentation.
- Add
Application.cfcvariables and CF Administrator settings to specifyhttpOnly,secure,domainfor session cookies (CFID, CFTOKEN, jsessionid) - Allow administrators to change the root ColdFusion Administrator username to something other than admin - Admin is always the default super user for ColdFusion administrator, it would be nice if you could specify an arbitrary username instead.
- Create an audit log for ColdFusion administrator changes.
- Improve ScriptProtect - I know this feature will always be insufficient, but alot of people use it. It could be improved quite a bit, it should at least block iframe tags!
- Remove the possibility of CRLF injection - Any tag that outputs headers (for example
cfheader,cfcontent,cfmail(subject attribute, or cfmailparam)) should strip the CRLF characters, so you can't inject new headers. Please vote for bug 83739 - Make addtoken=false default for cflocation - Whenever you do a cflocation it puts the session id's in the url query string. Users don't know that if they copy and paste the link somewhere it allows whoever visits the link to be logged in as them.
- Linux Installation scripts should detect SELinux and be able to install on SELinux. - You can still run ColdFusion on SELinux but it takes some configuration. (I provided some instructions in the ColdFusion 9 Lockdown Guide that I wrote)
If you like any of these ideas you can add them to this survey for ColdFusion 10, and feel free to post some more ideas in the comments!
10 Ideas to Improve Security in ColdFusion 10 was first published on June 18, 2010.
If you like reading about security, coldfusion, or cfml then you might also like:
- Fixinator and Foundeo Security Bundle
- CFSummit 2016 Slides
- Scope Injection in CFML
- Client Variable Cookie CFGLOBALS Includes Session Ids
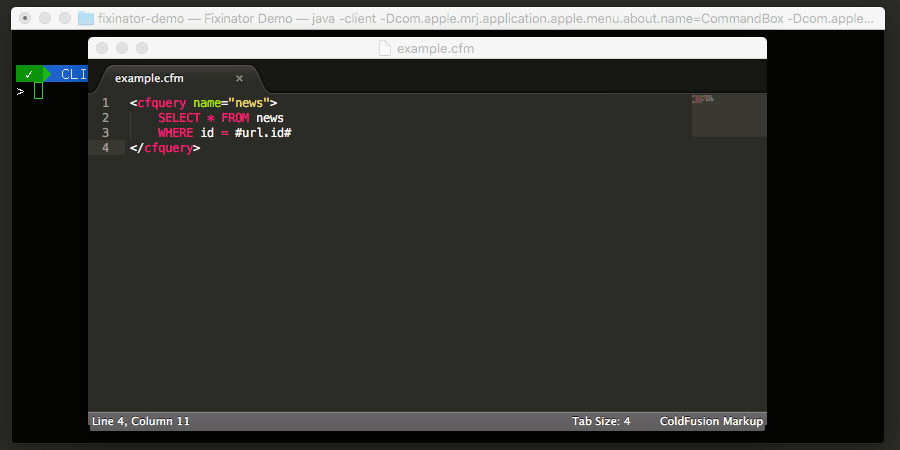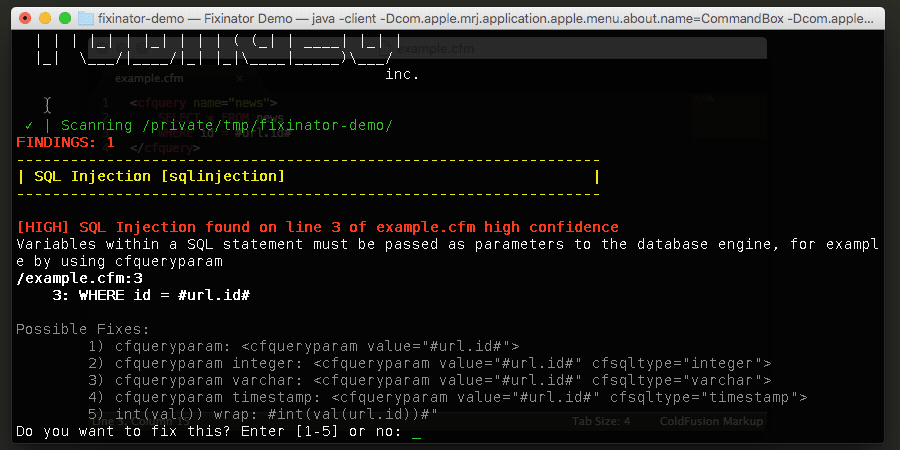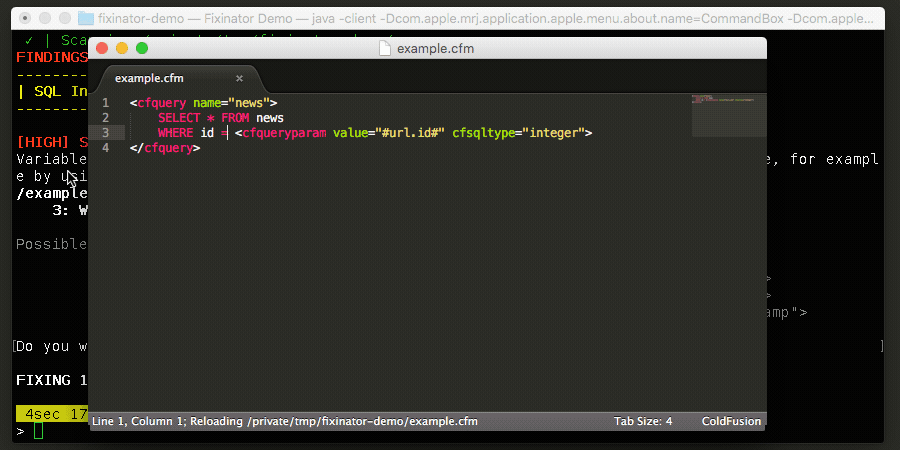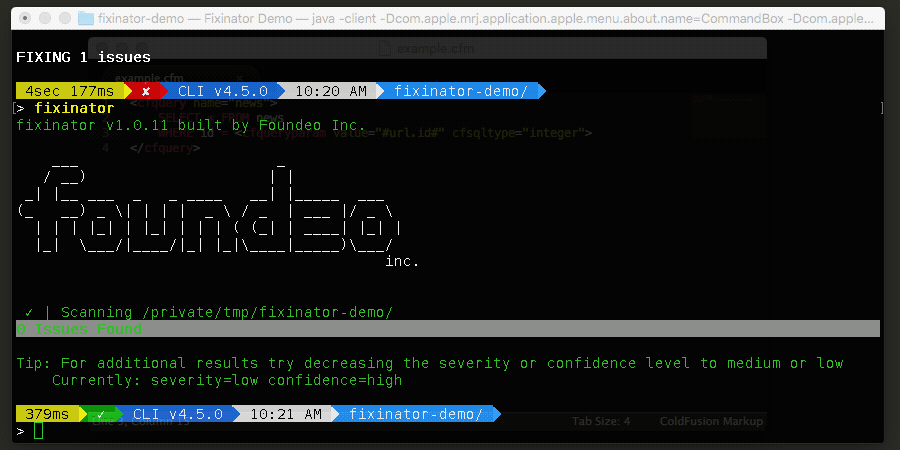
The Fixinator Code Security Scanner for ColdFusion & CFML is an easy to use security tool that every CF developer can use. It can also easily integrate into CI for automatic scanning on every commit.
Try Fixinator
CFBreak
The weekly newsletter for the CFML Community
Comments
I think #5 is already available in CF. Check http://help.adobe.com/en_US/ColdFusion/9.0/Admin/WSc3ff6d0ea77859461172e0811cbf364104-7ff4.html#WSc3ff6d0ea77859461172e0811cbf3638e6-7fc6
by Hemant on 06/19/2010 at 12:15:48 AM UTC
I have run into at LEAST 7/10 of these issues in the last 4 months. The biggest being the illusion of security from using scriptprotect.
by Mike Sewell on 06/19/2010 at 9:11:29 PM UTC
RE:#7 I agree that iframe should be blocked out of the box, but it's worth mentioning that scriptProtect can be extended in the cfusion/lib/neo-security.xml file.
Jason Dean has a comprehensive blog post about it here http://www.12robots.com/index.cfm/2008/9/9/Enhancing-ColdFusion-Script-Protection--Security-Series-10.
Amen on #9. Probably unlikely, though. The CF team takes backwards compatibility pretty seriously, and changing that would break any sites that rely on URL tokens.
Jason Dean has a comprehensive blog post about it here http://www.12robots.com/index.cfm/2008/9/9/Enhancing-ColdFusion-Script-Protection--Security-Series-10.
Amen on #9. Probably unlikely, though. The CF team takes backwards compatibility pretty seriously, and changing that would break any sites that rely on URL tokens.
by Dominic O'Connor on 06/28/2010 at 6:01:51 PM UTC
CF 9.0.1 (released today) has a minor security enhancement. Read more @ http://www.bytestopshere.com/post.cfm/security-enhancement-in-cf-9-0-1.
by Sami Hoda on 07/13/2010 at 12:55:12 PM UTC
@Dominic, if the CF team doesn't want to break backwards compatibility, couldn't a simple checkbox option suffice for the default. I haven't used the "addtokens='true'" on any cflocation in the 10 years of CF development. No cookies, no continue.
by Brandon Moser on 07/15/2010 at 7:32:31 PM UTC
 Pete Freitag
Pete Freitag